Visit blocked websites and browse anonymously
Updated9 December, 2021
Table of Contents
...Loading Table of Contents...Different tools avoid internet blocks in different ways, so they may be more or less successful in different situations. Try a few of the following, one at a time, at different times, to see what works in your region.
Test it first
- Test whatever tool you use to get around blocks while you have good access to the internet.
- First, look up your device's current IP address at a site like IPLocation or WhatIsMyIP.
- The address will be something in the format
192.168.10.1or2001:db8:0:1234:0:567:8:1. - Then, on that same device, turn on the app you want to use to get around internet blocks.
- Go back to the IP address lookup page you used and refresh it.
- Confirm that it now shows you a different address.
- If it shows you the same address as before, the app you are using has not hidden your address, and you could still be identified if you use it.
Learn why we recommend this
It is important to test that the app you use actually works and protects you so that you are ready when a website you need to visit is blocked. It is more difficult to ensure you are using a tool correctly in an emergency, and the websites where those tools can be downloaded are themselves frequently blocked.
Try a VPN
- See our page of tools under "Internet connection" for some recommended VPNs and their strengths. These include options for running your own VPNs.
- If your country blocks your VPN, you may have to find a new one. Identify a few VPN services that do what you need, that are safe to use in your region.
Learn why we recommend this
A VPN can make it look like your connection is coming from a different region or country. It can also protect your communications from snooping on your local wifi or at the servers of your internet provider. If your internet connection is like a tunnel, think of the VPN as a layer of armor around that tunnel.
Some VPN services rely on functionality that is built into the Windows, Mac, Linux, Android and iOS operating systems. Others require you to install and configure additional software (like OpenVPN or WireGuard). Some VPN providers will offer a customised installer that handles everything for you.
It is good to identify a few different VPNs you might use, in case one gets blocked, as basic VPNs often do not have the ability to resist blocking.
Try Tor
- See our Tor Browser guide tool guide.
Learn why we recommend this
Tor works similarly to a VPN, but instead of just sending your internet traffic to one service provider, it picks at least three servers to send your traffic through, hiding who has asked to see which pages. This protects your privacy better than a VPN. There are thousands of Tor servers, and they are run by volunteers around the world. Tor Browser is free and open source software.
Tor may be blocked or illegal to use in some countries. If Tor is blocked or unsafe to use in your country, you can use a Tor "Bridge".
Try a proxy service
- Try Lantern for Android, iOS, Linux, Mac, or Windows.
- Try Psiphon for Android, iOS, Mac, or Windows.
- If the download pages for Psiphon are blocked, you can email get@psiphon3.com, and they will send you an alternate link that may work.
- Be aware that Psiphon's Direct Download link for Android requires you to allow your device to Install Unknown Apps. Turning that permission on may make your device vulnerable to malware.
- Never use a web-based proxy.
Learn why we recommend this
If an internet filter in your area is blocking access to a certain site, or if that site does not allow access from the region where you are located, a proxy service can make it look like your request for a site is coming from or going to somewhere else, getting you around the block.
Psiphon3 is a secure, open source, public, anti-blocking tool that provides uncensored access to online content by using VPN and SSH proxies. Psiphon gets its funding from advertisers who pay to reach users with their ads.
Lantern is a secure, open source, public anti-blocking tool that uses HTTPS proxies to provide uncensored access to online content.
We recommend using these tools instead of a proxy that you access through your web browser (Firefox, Chrome, Edge, etc.). Web-based proxies work like a browser within a browser: it may look to you like there is another copy of, say, Firefox within a web page. Web-based proxies can be convenient if you can't install software on a computer you do not control, or when doing so might put you at risk. However, standalone tools like Psiphon and Lantern are trusted by experts to be more secure and reliable than web proxies.
Anonymity while browsing the Web
The best anonymity for browsing the Web comes with Tor Browser. See our Tor Browser guide
Learn why we recommend this
Internet servers providers (ISPs) can look at and record which websites you visit, but also websites you visit gather information about your location. In some countries ISPs have to store this information by law. Browsing anonymously protects you from ISPs knowing what sites you visit and also hide your true location so these sites can't track you.
VPN and proxy services give you a degree of anonymity while you browse the Web.
VPN encrypts all your traffic so your local internet service provider can not know what you are doing on the Internet. But some VPNs providers log all the traffic and can give out this information to a third parties. If you want to avoid this, choose well what VPN you use or you can create your own. Look at the tools section to see our VPN suggestions.
Proxy servers do not necessarily encrypt your connections. While they may prove effective way to visit blocked websites they may not make you anonymous or protect you from local ISP.
But, Tor Browser is encrypted and hops the connection at least 3 times from a proxy server to proxy server making it very hard for anyone (including those proxy servers) to know both where you are located and what servers you are accessing, making it the best choice.
Advanced: Partner with OONI
- If websites are blocked when accessing the internet in your region, the Open Observatory of Network Interference (OONI), which collects data from these situations around the world, would love to hear from you.
Ask these questions about other tools to visit blocked websites
We have provided a number of tools here you can use to stay connected to the internet despite blockages.
You may encounter other tools, recommended by friends or colleagues, and wonder whether they are safe and effective to use. We recommend having a look at the criteria we use to choose tools for Security in a Box as well as using the following criteria when judging the safety of tools.
When selecting proxies, consider the following:
Is it a web-based proxy, or standalone software that must be installed?
Web-based proxies can be convenient, at times — such as when you are unable to install software or when doing so might put you at risk — but reputable apps that work outside of your browser are both more secure and more reliable than proxies. If you must use a proxy through your browser, do not enter passwords or exchange sensitive information. Never use a web-based proxy with an address that begins HTTP instead of HTTPS, as it will leave your communication exposed to view.
Is it public or private?
Public proxies can be used by anyone, free-of-charge. However, if you do not know who is providing the proxy or why, it is possible it is being provided with malicious intent. Public proxies also tend to become overcrowded more quickly. This slows them down and increases the likelihood that they will be blocked. Private proxies limit access in some way, often by charging a monthly or yearly fee.
If you are able to get an account on a reliable, secure, trusted, private proxy, it will probably continue working longer than a public proxy.
How the internet works, and how some countries block websites
The internet is an international public resource, made up of computers, phones, servers, routers, and other devices connected to each other. It was designed to continue providing service even if part of the network was destroyed. "No one person, company, organization or government runs the internet." --Wikipedia, 2022
However, national and international bodies have some control over the infrastructure of the internet in their jurisdiction. Many countries prevent internet users within their borders from accessing certain websites or online services. Businesses, schools, libraries and other institutions may rely on similar filters to "protect" their employees, students and customers from material they consider harmful or distracting.
Internet filtering technology usually looks at the addresses that every phone, computer, router, and website uses to deliver you internet content, in order to block you from seeing certain sites or using certain services. Some filters block sites based on their IP addresses (strings of numbers that may be shaped like 192.168.1.1 or fc00::c549:f506:fc82:c77e). Others blacklist particular domain names (the addresses you may be more familiar with, like google.com or this website, securityinabox.org). Some filters block all addresses except an official whitelist of allowed sites defined by those controlling the internet. Other filters search through unencrypted internet traffic and cause the internet's infrastructure to ignore requests that include specific keywords (for example, searches that include "human rights violations" or names of opposition leaders).
You can often bypass these filters by installing software that uses intermediary servers, located in other countries, to pass content between the blocked content or service you are trying to reach and your device. The intermediary servers are often called proxies, and they come in many different forms.
Understanding how websites can be blocked
Research carried out by organisations like the Open Observatory of Network Interference (OONI) and Reporters Without Borders (RSF) indicates that many countries filter a wide variety of social, political and "national security" content, but rarely publish lists of what they block. Governments that wish to control their citizens' access to the internet also block proxies they are aware of, as well as websites that offer tools and instructions to help people get around filters.
Article 19 of the Universal Declaration of Human Rights guarantees free access to information. Despite this, the number of countries censoring the internet continues to increase. As this practice spreads throughout the world, however, so does access to anti-blocking tools that have been created, deployed, and publicised by activists, programmers, and volunteers, with funding from the United States, Canada, the European Union, NGOs, and other bodies concerned with free speech.
Your internet connection
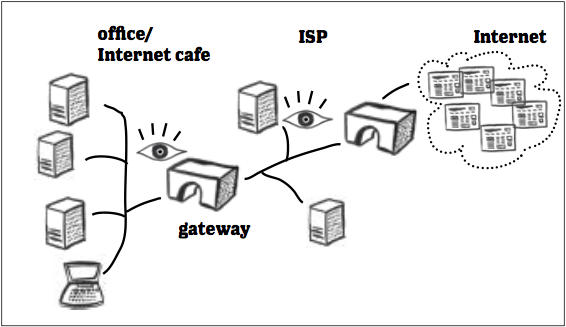
When you ask your computer to access a website, or your phone to use an app, your connection request and the content you see both go through a number of other computers. Your phone or computer first uses its wired, wireless or mobile data connection to reach the internet Service Provider (ISP). If you are home and using your own wifi, the ISP may be the company you pay for internet service. If you are using mobile data, the ISP you are connecting to is probably your mobile service provider. If you are working from an office, school, internet cafe, or some other public space, it may be difficult to determine who the ISP is.
Your ISP relies on the network infrastructure in your country to connect its users with the rest of the world. The ISP assigns an external IP address to the network you are on, whether it is your mobile phone's network, your wifi network, or the network of the internet cafe, school, or hotspot you are using. Your ISP will use this address to send content to your device. On the other end of your connection, the website or internet service you are accessing will have received its own IP addresses from an ISP in its own country.
Online services can use this address to send you the webpages you are trying to view and other data you request. (Your device has its own IP address, as well, which is how your router sends everybody on your network their own traffic. It is only used on your local network.)
Anyone who learns your IP address can figure out what city or region you are in. Certain institutions can determine your precise location even more precisely:
- Your mobile provider knows the precise physical location of your phone while your device is on, by triangulating your location between its cell towers.
- Your ISP will likely know what building you are in.
- An internet cafe, library, or business where you are accessing the internet will know which of their computers you were using at any given time. Or, if you are using your own device, they will know which local IP address was assigned to your device on their local network, thus associating all your activities to your device.
- Government agencies may know all of the above. And, even if they do not, they can often use their influence to find out.
Internet communication is somewhat more complex than the description above, but even this simplified model can help you decide which anti-blocking tools to use.
How websites are blocked
When you view a web page, your device uses the Domain Name Service (DNS) to look up the IP address (something like 172.105.249.143) associated with the website's domain name (something like securityinabox.org). It would then ask your ISP to send a request to the ISP in charge of 172.105.249.143. If that request is successful, your device asks the webserver at 172.105.249.143 for the contents of securityinabox.org.
If you are in a country that censors securityinabox.org, your request will not succeed at some point during that process. This could happen at one of a number of points in the process: when your device tries to look up the IP address, when it requests the content, or as the content is being sent to your device. In some countries, ISPs are required to consult a national blacklist of sites they must not show you. Other countries compare all requests from within the country to a centralised blacklist and use their own infrastructure to filter them out. Blacklists can contain domain names, IP addresses, keywords, or all of the above. Keyword filters scan both unencrypted requests to see sites, and the results a website or service returns to you.
You might not always know when you have requested a blocked webpage. Some filtering tools display a message that explains why a particular page has been censored. Others display misleading error messages. They may say the page cannot be found, for example, or the address was misspelled.
Each blocking technique has strengths and weaknesses. When attempting to get around internet blocks, it is easier to assume the worst than to figure out what techniques are being used in your country. You might as well assume:
- That blocking is implemented nationally, at the ISP level and on your local network;
- That DNS lookups and content requests are blocked;
- That blacklists are maintained for both domain names and IP addresses;
- That your unencrypted internet traffic is monitored for keywords; and
- That you will be given a misleading reason when a blocked site fails to load.
The safest and most effective anti-blocking tools should work regardless of the type of block you are facing.
How tools get around blocks
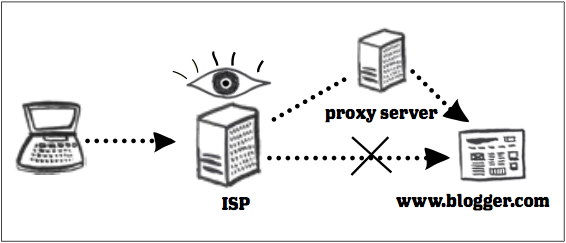
Tools like Tor and VPNs apply encryption to your traffic, thus protecting the secrecy of the requested data, including the IP address of the requested service. They hide the address until your request arrives at a proxy server in another country. The proxy then decrypts that address, sends your request to see the content, accepts the response from the page or service, encrypts it again, and sends it back to your device. We sometimes use "tunnels" as a metaphor for this: your traffic is still passing through infrastructure controlled by the ISP, government, or other institution that wants to block your access, but their filters are unable to read the content of your request or determine exactly where you're trying to go when you leave the tunnel. All they know is that you are interacting with a proxy and that encryption is being used to prevent them from seeing the information you're requesting.
Blocking resistance
Of course, the government agency in charge of internet filters — or the company that provides your government with blocking software — might eventually identify that unknown computer as a proxy, and add it to their blacklist. This is why VPNs and other tools sometimes stop working.
It usually takes time for those blocking the internet to discover proxies, however. Tools for visiting blocked websites use one or more of the following techniques:
- Hidden proxies can be distributed to users in a way that prevents censors from finding them all at once.
- You can create private proxies, using Outline or Algo, limiting the number of people who know about and can access them, and making it harder for authorities to find and block them.
- Disposable proxies can be replaced more quickly than they can be blocked.
- Obfuscation keeps censors from identifying unknown proxies by observing details ("metadata") about the otherwise unreadable traffic to and from them.
- Domain fronting makes it so blocking an address also blocks access to some other useful, popular service (such as Google).