Security-in-a-box blog
By Security in a Box | 2025.06.05
Two new guides on safer travels and TikTok, a search engine, an RSS feed, a complete update of all guides, a new section, and updated tool guides on Instagram and X.
延伸阅读
By Security in a Box | 2025.03.18

Tips on leaving X and moving to alternative platforms
延伸阅读
By Security in a Box | 2025.02.18

Updates to tool guides on password managers, browser add-ons, and basic Android security.
延伸阅读
By Haven | 2025.02.12

点心指南:为中文读者提供的数字安全建议
延伸阅读
By Security in a Box | 2024.11.28

A few first effective steps you can take to better protect your device
延伸阅读
By 穆罕默德·马斯卡蒂 | 2021.07.23

国际特赦组织和媒体平台“禁忌的故事”发表了以色列使用一种工具监视世界上许多人的调查。这项调查被称为飞马项目。
延伸阅读
By Gus Andrews | 2021.03.24

综合介绍有关整体数字安全、物理安全,以及组织安全、隐私,和健康的各类资源。可以按语言、社群,或者话题浏览。
延伸阅读
By Gus Andrews | 2021.02.01

Updates to tool guides on password managers, browser add-ons, and basic Android security.
延伸阅读
By Maria Xynou & Chris Walker | 2016.05.23
WhatsApp's collaboration with Open Whisper Systems recently brought end-to-end encryption to the lives of a billion people around the world. (Open Whisper Systems develops Signal, an open source mobile messaging and VoIP app.) When WhatsApp integrated the encryption protocol developed for Signal, many of us began using end-to-end encryption without even realizing it.
延伸阅读
By Maria Xynou | 2015.12.03
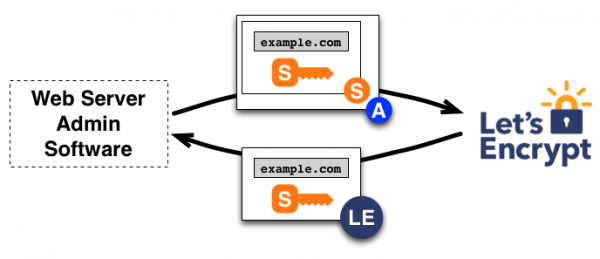
Do you own a website? If so, as of today Let's Encrypt, a new non-profit certificate authority (CA), entered Public Beta and allows you to add HTTPS to your website for free and more easily than ever before.
延伸阅读
By Maria Xynou | 2015.10.08

In the last week, critical security flaws have been reported in TrueCrypt, the open source software for file and disk encryption. As a result, we are reviewing our advice on file and disk encryption and we now recommend users to consider other tools for secure file storage.
延伸阅读
By Front Line Defenders | 2015.03.13

The Workbook on Security is designed to raise awareness about security issues and to help human rights defenders consider how to mitigate threats. The workbook takes human rights defenders through the steps to producing a security plan - for individuals and for organisations.
延伸阅读
By Spyros E. Monastiriotis | 2015.03.13

Uganda has been in the news headlines around the world since 2009, when it introduced its first Anti-homosexuality Bill and there have been several attempts since then to increase penalties for LGBT people and those who help them.
延伸阅读
By Chris Walker | 2015.03.11

In light of ongoing revelations about the global surveillance efforts of the US National Security Agency (NSA) and its intelligence allies, you might be wondering if any of this really matters anymore. Much of the recent media coverage appears to suggest that, not only are They recording everything we do and say on the Internet, but now They've defeated our encryption.
延伸阅读
By Kaustubh Srikanth | 2015.01.06

On 17th December 2014, the Government of India's Ministry of Communications and Information Technology issued an order to all licensed Internet Service Providers (ISPs) in the country to block access to 32 websites, effective immediately.
延伸阅读














