Security-in-a-box blog
By Security in a Box | 2025.06.05
Two new guides on safer travels and TikTok, a search engine, an RSS feed, a complete update of all guides, a new section, and updated tool guides on Instagram and X.
Leia mais
By Security in a Box | 2025.03.18

Tips on leaving X and moving to alternative platforms
Leia mais
By Security in a Box | 2025.02.18

Updates to tool guides on password managers, browser add-ons, and basic Android security.
Leia mais
By Haven | 2025.02.12

Introducing the Dim Sum guide, a resource that builds on the content of Security in a Box and provides more specific instructions and guidance for Chinese-speaking readers from China
Leia mais
By Security in a Box | 2024.11.28

A few first effective steps you can take to better protect your device
Leia mais
By Mohammed Al-Maskati | 2021.07.23

A Anistia Internacional e a plataforma de mídia Forbidden Stories publicaram uma investigação sobre o uso de uma ferramenta israelense utilizada para espionar uma enorme quantidade de pessoas no mundo. A investigação foi chamada de Projeto Pegasus.
Leia mais
By Gus Andrews | 2021.03.24

Introducing an overview of resources on holistic digital, physical, and organizational security, privacy, and wellbeing. Viewable by language, community, and topic.
Leia mais
By Gus Andrews | 2021.02.01

Updates to tool guides on password managers, browser add-ons, and basic Android security.
Leia mais
By Maria Xynou & Chris Walker | 2016.05.23
WhatsApp's collaboration with Open Whisper Systems recently brought end-to-end encryption to the lives of a billion people around the world. (Open Whisper Systems develops Signal, an open source mobile messaging and VoIP app.) When WhatsApp integrated the encryption protocol developed for Signal, many of us began using end-to-end encryption without even realizing it.
Leia mais
By Maria Xynou | 2015.12.03
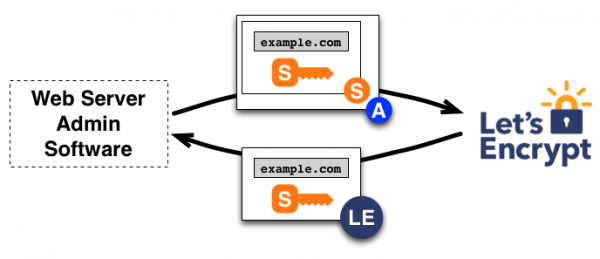
Do you own a website? If so, as of today Let's Encrypt, a new non-profit certificate authority (CA), entered Public Beta and allows you to add HTTPS to your website for free and more easily than ever before.
Leia mais
By Maria Xynou | 2015.10.08

In the last week, critical security flaws have been reported in TrueCrypt, the open source software for file and disk encryption. As a result, we are reviewing our advice on file and disk encryption and we now recommend users to consider other tools for secure file storage.
Leia mais
By Front Line Defenders | 2015.03.13

The Workbook on Security is designed to raise awareness about security issues and to help human rights defenders consider how to mitigate threats. The workbook takes human rights defenders through the steps to producing a security plan - for individuals and for organisations.
Leia mais
By Spyros E. Monastiriotis | 2015.03.13

Uganda has been in the news headlines around the world since 2009, when it introduced its first Anti-homosexuality Bill and there have been several attempts since then to increase penalties for LGBT people and those who help them.
Leia mais
By Chris Walker | 2015.03.11

In light of ongoing revelations about the global surveillance efforts of the US National Security Agency (NSA) and its intelligence allies, you might be wondering if any of this really matters anymore. Much of the recent media coverage appears to suggest that, not only are They recording everything we do and say on the Internet, but now They've defeated our encryption.
Leia mais
By Kaustubh Srikanth | 2015.01.06

Em 17 de dezembro de 2014, o Ministério das Comunicações e Tecnologia da Informação do Governo da Índia emitiu uma ordem para todos os Provedores de Serviço de Internet (ISPs) licenciados no país bloquearem o acesso a 32 sites, com efeito imediato.
Leia mais














