انترنېټ څنګه کار کوي او څنګه سانسورېدای شي
فهرست
انترنېټ څنګه کار کوي او څنګه ځینې هېوادونه او بڼسټونه کولای شي چې وېب پاڼې او آنلاین خدمتونه بند یا سانسور کړي
انترنېټ په نړېواله کچه یوه عامه سرچینه ده او ترکیب کې یې کمپیوټرونه، ټیلفونونه، سرورونه، راوټرز او نور ډیوایسونه (devices) شامل او یو له بل سره نښنلېدلي دي. انترنېټ داسې دیزاین شوی چې که له دې ډیوایسونو څخه یو یې هم له کاره ولویږي، انترنېټ به د آنلاین خدمتونو وړاندې کولو ته ادامه ورکوي او کوم خنډ سره به نه مخ کیږي.
انترنېټ له وګړي، شرکت، سازمان، او یا کوم دولت له لورې نه اداره کیږي.
د انترنېټ حکومتوالۍ په اړه د ویکیپیدیا پاڼه
خو له دې سره هم، ملي او نړېوال بڼسټونه به خپلو سیمو کې د انترنېټ پر زېربنا باندې یو څه کنترول لري. ډېری هېوادونه ځینو مشخصو وېب پاڼو او آنلاین خدمتونو ته د انترنېټ کاروونکو لاسرسۍ محدودیوي. شرکتونه، ښوونځي، کتابتونونه او نور سازمانونه هم «د خپلو کارکوونکو»، زدکوونکو او یا پیرودونکو د «خوندیتوب» په موخه پر ورته فلترونو اتکا کوي تر څو دوی د هغو مواردو پر وړاندې خوندي وساتي چې د نوموړي بڼسټ لخوا زیانمنونکې او ناوړه ګڼل کیږي.
پر انترنېټ د فلتر لګولو څرنګوالی د تکنالوژی په نوعیت پورې اړه لري. ځینې
فلترونه د IP آدرس له مخې لګول کیږي (لکه هغه د پېژندنې شمېرې چې ظاهري بڼه
یې172.105.249.143 یا 2a01:7e01::f03c:92ff:fecd:7e45 غوندې وي؛ له ټیلفون،
کمپیوټر، رواټرز، یا وېب پاڼه سره نښلېدلی او کاروونکو ته د دوی له غوښتنې سره
سم مالومات برابروي). ځینې نور یې پر مشخص ډومینونو (لکه google.com یا
securityinabox.org) باندې فلتر لګوي. او ځینې نور فلترونه غیر له رسمي
سایټونو نه چې له اړوندې ادارې لخوا منل شوي وي، نور ټول یې بلاک کوي. او
بلاخره ځینې نور فلترونه د انکرېپټ شوي انترنېتي ترافیک له لارې لګول کیږي چې
په ترځ کې یې انترنېټ زېربنا د کاروونکو (یوزرز) لخوا هغه غوښتنې له پامه
غورځوي چې به جوړښت کې یې ځینې منع کړل شوي کلمې (لکه د «بشري له حقونو
سرغړونې» او یا د اپوزېسیون ډلې د مشرانو نومونه) پکښې شامل وي.
تاسو کولی شئ چې د هغو سافټویرونو په مرسته چې د بل هېواد سرورونو له لارې فعالیت کوي، له دغو محدودیتونو تیر شئ او د اړتیا وړ مواد او آنلاین خدماتوته لاسرسۍ پیدا کړئ. د نوموړي سافټویرونو په اړه نور مالومات دلته ولولئ: د پر وېب پاڼو له لګول شویو محدودیتونو او څارنو څنګه تېرې دی شو.
د وېپ پاڼو او آنلاین خدمتونو د بندېدو څرنګوالی
د Open Observatory of Network Interference (OONI) او بې پوله خبریالانو (RSF) له لورې څېړنې ښیي چې ډېری هېوادونه پر ټولنیزو، سیاسي، او «ملي امنیت» اړوند محتویاتو باندې فلتر لګوي خود دوی هیڅکه د فلتر وړ د محتویاتو نوملړ نه خپروي. هغه دولتونه چې غواړي د خپلو وګړو لاسرسۍ انترنېت ته محدود کړي، VPNs او یا ورته ابزار یا هغه وېب پاڼې هم بندوي چې د سانسور پر وړاندې د حل لارې وړاندې کوی.
د بشر د حقونو د نړیوالې اعلامیې ۱۹مه ماده معلوماتو ته د وړیا لاسرسي ضمانت ورکوي۔ سره له دې، د هغو هېوادونو شمېر مخ په زیاتېدو دی چې پکښې انترنېت له سانسور سره مخ دی. هرڅومره چې د سانسور هڅې زیاتیږي، هغومره د هېوادونو لکه د امریکا متحده ایالتونو، کانادا، اروپایی اتحادیې، او همدارنګه د انجوګانو او نورو بنسټونو په بسپڼه د فعالانو، رضاکارانو او پروګرامرانو په مرسته د سانسو-ضد ابزارو ته لاسرسۍ زیاتیږي.
ستاسو د انترنېټ اړیکه
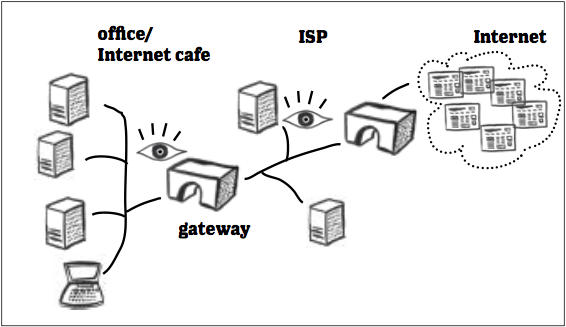
کله چې غواړئ کمپیوټر کې یوه وېب پاڼه خلاصه کړئ او یا د ټېلفون له لارې یو اپلېکېشن خلاص کړئ، نو ستاسو غوښتنه د څو نېټورک وسیلو له لارې تیریږي. لومړۍ، ستاسو کمپیوټر یا ټیلفون به له سیم داره، بیسیمه، او یا د mobile data سره اړیکه نیسي او بیا به ستاسو د انترنت چمتوکوونکی (ISP) ته ستاسو غوښتنه رسوي. که تاسو د کور انترنت (وای-فای) کاروئ، نو کېدای شي چې ستاسو ISP هغه کمپنۍ وي چې انترنېت مو ترې پېرودلی. او که د تیلفون انترنېټ (mobile data) کاروئ نو ستاسو ISP هغه کمپنۍ ده چې سیم کارت مو ترې پېرودلی. خو که له دفتر، ښوونځي او یا انترنېت کافه او نورو عامه ځایونو څخه انترنېت کاروئ نو دا به ستونزمنه وي چې خپل ISP وپېژنئ او یا پوه شئ چې له کوم ISP سره ستاسو الکترونیکي وسیله نښلېدلي ده.
ISP ستاسو په هېواد کې له نېټورک زېربنا سره باید تړاو ولري ترڅو د انترنېت کاروونکي له نړۍ سره ونښلیږي. په دې توګه، ISP، سیمه ییز نېټورک ته او یا ستاسو الکترونیکي وسېلې لپاره -هغه که له وای-فای سره وصل وي، ستاسو د تېلفون له انترنېت سره او یا په کوم انترنېت کافې کې له انترنېت سره نښلېدلی وي- یو IP جوړوي. کله چې آی-پی آدرس جوړ شو، ISP له همدې آدرسه تاسو ته اړتیا وړ محتویات ستاسو الکترونیکي وسېلې ته لیږدوي. د انترنېت اړیکې بلې خواته، وېب پاڼې او آنلاین خدمتونه خپل ځانګړی IP آدرس له هغې ISP څخه ترلاسه کوي، چې د دوی په هېواد کې نصب شوي وي.
آنلاین خدمتونه د همدې آدرس له لارې تاسو ته هغه وېب پاڼې یا ډېټا لېږدوي، چې تاسو یې غوښتنه کړي وه. (ستاسو الکترونیکي وسیله خپل ځان ته IP آدرس لري او له همدې آدرس څخه، ستاسو راوترز هرچاته د انترنېت ټرافیک لېږدوي. د ډېټا دا ډول انتقال یوازې په سیمه ییزه نېټورک کې ترسره کیږي.)
هغه څوک چې ستاسو IP آدرس لري، پوهیږي چې تاسو چېرته مېشت یاست او یا له کوم ځای څخه انترنېټ سره وصل شوي یاست. ځیني مشخصې ادارې بیا حتی ستاسو دقیق آدرس هم ستاسو له IP آدرس څخه پیدا کولی شي:
- هغه شبکې چې ګرځنده موبایل مو ترې پېرودلی، کولی شي چې ستاسو فزیکي موقعیت ستاسو د تیلفون له لارې پیدا کړي. دوی دا کار د تیلفون ستنو تر منځ ستاسو د فزیکي موقعیت ترانګیولیشن له لارې ترسره کولی شي.
- ستاسو د ISP له مخې ستاسو د هستوګنې تعمیر په ډاګه کېدای شي.
- که له انترنېت کافې، کتابتون یا د کار ځای څخه انترنېټ سله وصلیږئ، دوی کولی شي ووایي چې تاسو څه وخت له کوم کمپیوټر څخه انترنېت سره وصل وئ. او که تاسو ددوی انترنېت له خپلې شخصي الکترونیکي وسیلې سره ونښلوئ، دوی به پوهیږي چې کوم سیمه ییز IP آدرس ستاسو الکترونیکي وسیلې لپاره ځانګړی شوی و، او د آی-پی آدرس له مخې ستاسو د الکترونیکي وسیلې فعالیت څارلی شي.
- دولتي څانګې هم په پورتنیو ټولو مواردو باندې پوهیږي. خو که دوی په دې مواردو باندې پوه نه شي، دوی کولای شي د نفوذ له لارې ستاسو په هکله مالومات ترلاسه کړي.
انترنېټې اړیکې تر هغه څه چې مخکې وویل شول، پېچلې دي. خو بیا هم دا ډول ساده توضیح کولای شي تاسو په ډاګه کړي چې که تاسو انترنیت سره وصل کیږي کوم ډول ګواښونو سره به مخ وئ او یا کوم سازمان یا بنسټ ستاسو د اړتیا وړ وېب پاڼې بند کړي دي.
څنګه وېب پاڼه بندیږي (بلاک کیږي)
کله چې یوه وېب پاڼه خلاصوئ، ستاسو الکترونیکي وسېله له ډومېن نوم خدمت (domain
name service -DNS) سره وصلیږي تر څو په نوموړي DNS پورې اړوند د IP آدرس
ترلاسه کړي- د بېلګې په توګه، ستاسو الکترونیکي وسیله له DNS څخه د
securityinabox.org اړوند د IP آدرس غواړي؛ چې بیا، د 172.105.249.143 ځواب
ترلاسه کوي. وروسته، ستاسو الکترونیکي وسیله له ISP څخه غواړي چې د
172.105.249.143اړوند ISP څخه وغواړي تر څو په 172.105.249.143 کې له وېب
سرورو څخه د securityinabox.org اړوند مالومات راټول کړي.
که داسې هېواد کې هستوګن وئ چې securityinabox.org ته لاسرسۍ یې بند کړی وي، ستاسو غوښتنه به د دې پروسې په یوه برخه کې له خنډ سره مخ شي. دا کېدای شي هغه برخه وي: کله چې ستاسو الکترونیکي وسیله د IP آدرس ترلاسه کوي، کله چې ستاسو الکترونیکي وسیله آنلاین مواد ترلاسه کوي، او یا کله چې آنلاین مواد ستاسو الکترونیکي وسیلې ته د لیږد په حال کې وي. په ځینو هېوادونو کې، ISPs داسې اعیار شوي وي چې مخکې له دې چې تاسو ته وېب پاڼه درښکاره کړي، د هېواد لخوا له جوړ شوي تور لېست سایټونو سره مشوره کوي. له دغه تور لېست کې کېدای شي سایټونه د ډومېن ځینې نومونه، IP آدرسونه، کلیدي ټکي او کلمې شاملې وي. فلترونه کولی شي هم ناانکرېپټ شوي غوښتنې او هم ستاسو الکترونیکي وسیلې ته د حاصل شوي وېب پاڼو یا آنلاین خدمتونو لېږد بند کړي.
تاسو به تل نه پوهیږئ چې کوم وېب پاڼه، موارد یا آنلاین خدمتونه د لاسرسۍ وړ نه دي او یا بند دي. داسې هم کیږي چې کله یوه سانسور شوي وېب پاڼه خلاصوئ، تاسو ته پاڼه په ځواب کې وایي چې ستاسو د اړتیا خدمت یا وېب پاڼه سانسور شوي ده او په دې اړه توضیحات به هم درکوي. خو په ډېرو مواردو کې تاسو له ناسم ځواب سره مخ کیږئ. د بېلګې په توګه، ستاسو پر سکرین به دا جمله راځي: ستاسو د اړتیا وړ پاڼه یا آنلاین خدمت پیدا نه شوه، او یا آدرس مو سم نه دی لیکلئ.
د سانسور هر تخنیک کېدای شي د ځواک او ضعف ټکی ولري. کله چی غواړئ د سانسور ماتولو په مرسته د اړتیا وړ خدمتونو یا وېب پاڼې ته لاسرسۍ پیدا کړئ، د دې پرځای چې پوه شئ چې د سانسور څه ډول تخنیک کارول شوی، تاسو به د منفي پایلو په اړه ډېر فکر کوئ. همدارنګه تاسو به د لاندو مواردو په اړه هم فکر کوئ:
- چې آیا سانسور د هېواد په کچه، پر سیمه ییزه نېټورک کې د ISP په کچه (ISP level and on your local network) پلې شوی دی،
- چې آیا د DNS سره ارتباط او د آنلاین خدمتونو ترلاسه کول (DNS lookups and content requests) بلاک شوي دی،
- چې آیا سانسور د ډومېن نومونو او IP آدرسونو لپاره وضع شوی دی،
- چې آیا ناانکرېپټ شوی انترنېت ترافیک د کلیدي ټکو د کارولو له لارې څارل کیږي، او
- هیڅ نښه یا دلیل به د بندېدو لپاره نه ورکول کېږي.
په هر حال، د سانسور ماتولو خوندي او موثره ابزار باید تاسو لپاره په هر حالت کې نتیجه ورکړي.
د سانسور ماتولو ابزار څنګه کار کوي
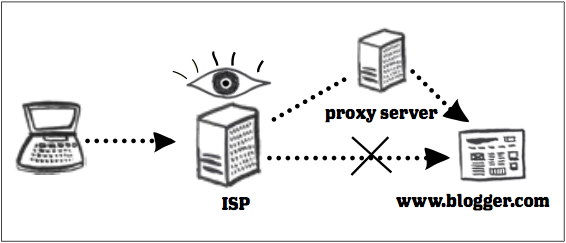
Tor اوVPN غوندې د سانسور ماتولو ابزار د انترنېت جریان انکرېپټوي، او په دې توګه د IP آدرس په شمول، اړونده د ډېټا خوندي کوي. دغه ابزار ستاسو آدرس تر هغې پټ ساتي چې ستاسو غوښتل شوي مالومات په بل هېواد کې پراکسي سرور ته ورسیږي. وروسته بیا، د پراکسي سرور نوموړی آدرس انکرېپټ کوي، تاسو ته د لاسرسي پیغام درکوي تر څو تاسو یې ومنئ. له منل کېدو وروسته، نوموړي پاڼه یا آنلاین خدمت بیاځلي انکرېپټ کیږي او ستاسو الکترونیکي وسیلې ته لېږدول کیږي. اکثراً کارپوهان دې پروسې ته د «تونل» اصطلاح کاروي: یانې ستاسو انترنېټی جریان د ISP په مرسته کنترولي شوي زېربنا څخه تیږیږي، دولت یا ستاسو اداره غواړي چې ستاسو لاسرسي باندې محدودیت ولګوي، خو د دوی فلترونه نه شي کولی چې ستاسو د غوښتنې محتویات ولولي او یا وروسته له دې چې د انترنیت جریان له تونل څخه ووځي، دا مالومات به چېرې لیږل کېږي. دوی به یوازې په دې پوهیږي چې تاسو له یو پراکسي سرور سره په تماس کې یئ او تاسو انکرېپشن کارولئ تر څو د دوی د څارنې هڅې بی ګټی شي.
د مقاومت بلاک کول
له یاده مه باسئ چې، د انترنېټ سانسورولو اړوند دولتي اداره او یا هغه کمپنۍ چې دولت لپاره د سانسور او بلاکولو سافټویرونه جوړوي، په نهایت کې په دې پوهیږي چې یو ناپېژند کمپیوتر جریان ته ننوتلی، او دوی یې باید د بلاک نوملړ ته واستوي. په دې صورت کې کله وار د VPN کارول نتیجه نه ورکوي.
په ټولییزه توګه، د انترنېټ سانسورولو ادارې نه شي کولای چې په لنډ وخت کې د انترنېټ په جریان کې د ناپېژند الکترونیکي وسیلو شتون په ډاګه کړي. د سانسور ماتولو ابزار له لاندې څخه یو یا څو تخنیکونه کاروئ تر څو ژر و نه پېژندل شي:
- پټ پراکسي د انترنېت کاروونکو ته وېشل کیږي تر څو د سانسور لګولو ادارو لخوا و نه پېژندل شي.
- خصوصی پراکسي د د کاروونکو شمیر محدود ښیي او د سانسور لګولو ادارو ته د دوی پېژندل ستونزمنوي. تاسو کولی شئ چې خصوصي پراکسي جوړ کړئ او په دې اړه لاندې بېلګه وګورئ: Outline or Algo.
- مؤقت پراکسي ژر بدلیدی شي (تر دې چې بلاک شي).
- Obfuscationکولای شي چې پراکسي جریان (ترافیک) د انترنېت یو عادي جریان په توګه تمثیل کړي او د سانسور لګولو ادارو ته د عادی او پراکسی جریان ترمنځ توپیر ستونزمنوي.
- Domain fronting د وېب د آدرس بلاکول ستونزمنوي ځکه چې بلاکول کېدای شي ځیني ګتورو سایتونو (لکه ګوګل سایت) ته لاسرسی محدودوي.